See? 39+ Facts About Fine Grained Access Control People Forgot to Tell You.
Fine Grained Access Control | Fgac is a mechanism for deploying a transparent security policy on tables, which oracle will use to rewrite the submitted query and add your security policy predicate information. Of course, access control can prevent access to sensitive information, but it can also help you build applications that depend on open distro for elasticsearch for search. Implementing fine grained access control using policy function and dbms_rls package. The entity that wants to access the data item needs to provide its credentials to a policy enforcer. Oracle 11g introduces fine grained access to network services using access control lists (acl) in the xml db repository, allowing control over which access control lists can be created, amended and deleted in the xml db repository directly using ftp or webdav.
Fine grained access control arup nanda, proligence, inc. We will show two approaches to using neo4j security features to support the. One complex solution is to create a set of views and synonyms on this master tables and manage. This results in separation of concerns for the access control to the data and the data itself. Integration with ldap directory services.

This results in separation of concerns for the access control to the data and the data itself. Either extremely simplistic, or overly complex and challenging for even security experts to use. In this type of schemes, each data item is given its own access control policy. Integration with ldap directory services. It allows a finer level of access control than the standard db2 permissions scheme. This article shows solutions to avoid cluttering of sql. How would you provide a selective access to columns and rows of one table to multiple database or applicative users ? The default control of access to the oracle database semantic data store is at the model level: Grant select on cost_center to public; The concept of the policy type for databases is proposed. Of course, access control can prevent access to sensitive information, but it can also help you build applications that depend on open distro for elasticsearch for search. This is done this way for demo purposes only. When used alone, application context can serve as a secure data cache.
Let's explore this a little more. Fine grained access control (fgac). Grid access control policy languages today are generally one of two extremes: Fine grained access control arup nanda, proligence, inc. The default control of access to the oracle database semantic data store is at the model level:
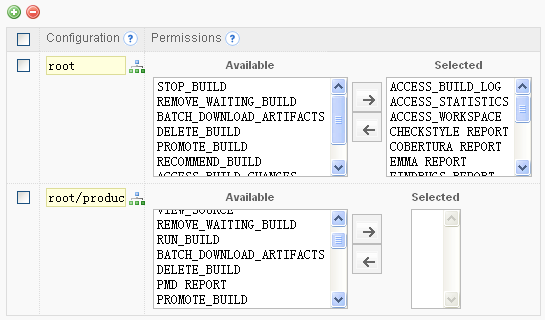
We will show two approaches to using neo4j security features to support the. In this paper, we explicitly identify requirements for an access control policy language for grid data and then consider six. Fine grained access control (fgac). This cache saves the repeated overhead of querying the. Implementing fine grained access control using policy function and dbms_rls package. One complex solution is to create a set of views and synonyms on this master tables and manage. The transaction manager consults this list during the voting phase of the commit protocol and votes to abort. This type of access control is typically used in cloud computing, where often a large quantity of data types and data sources may be stored together but each data item must be accessed based on different criteria. This results in separation of concerns for the access control to the data and the data itself. Fine grained access control arup nanda, proligence, inc. Grant select on exp_report to public; Introduction just as a picture is worth thousand words, it's my belief that even the most complex of concepts or features can be easily explained through an example, where the reader has the ability to test out the concepts while reading. Create context app1_ctx using app1_ctx_package
Create an open access policy, as shown in figure 7, which doesn't specify a principal and so doesn't require request signing. Integration with ldap directory services. This results in separation of concerns for the access control to the data and the data itself. The default control of access to the oracle database semantic data store is at the model level: Basically, you don't want your business code be dependent on the fgac implementation, you don't want to mix fgac code in where clause of the select statements of your business rules.

Grid access control policy languages today are generally one of two extremes: Fine grained access control (fgac). This article shows solutions to avoid cluttering of sql. Create context app1_ctx using app1_ctx_package The concept of the policy type for databases is proposed. The default control of access to the oracle database semantic data store is at the model level: Fine grained access control arup nanda, proligence, inc. The default control of access to the oracle database semantic data store is at the model level: In addition, oracle provide the. Oracle fine grained access control demo. Implementing fine grained access control using policy function and dbms_rls package. This is done this way for demo purposes only. Either extremely simplistic, or overly complex and challenging for even security experts to use.
Fine Grained Access Control: Let's explore this a little more.
Source: Fine Grained Access Control
0 Response to "See? 39+ Facts About Fine Grained Access Control People Forgot to Tell You."
Post a Comment